
We’ve all been conditioned to view cyber threats as external threats: faceless hackers breaking in from the outside. However, sometimes the risk may actually be within your charity, as in the case of insider threats.
Insider threats refer to security risks that come from within your own organisation, whether it’s a disgruntled employee, a well-meaning volunteer who makes a mistake, or a third-party contractor with access to sensitive systems.
The takeaway? No charity is exempt. Even with a small team and tight budget, the digital doors can still swing open from the inside. From donor data, financial records, to internal communications, your organisation holds valuable information, and it’s your responsibility to keep it safe.
In this blog, we’ll explain what insider threats are, why they’re on the rise within the charity sector, and what practical steps your organisation can take to protect itself. If you’re responsible for safeguarding digital assets, donor trust, and operational continuity, this is a conversation you must be part of.
Insider Threats Statistics: Charities at Risk
These threats are often difficult to detect, and their consequences can be just as damaging, if not worse. And the scale of the problem is growing. According to the 2023 Ponemon Insider Threat Report, the average cost of an insider risk jumped to $16.2 million per organisation, taking an average of 86 days to detect and contain.
A recent report revealed that 29% of insider-related incidents cost organisations over $1 million to remediate. Add to that the intricacy of modern IT systems, increased reliance on cloud tools, and under-resourced security policies, and it’s easy to see how insider risks can quietly escalate.
90% of cybersecurity professionals now believe their organisations are vulnerable to insider threats, and 71% of organisations feel at least moderately exposed to these internal dangers. The most common culprits? Overly complex systems (39%) and patchy security controls (33%).
Insider Threats in Cybersecurity: Definition & Practical Examples
Insider threats aren’t just about intentional sabotage; they also include accidents, negligence, or poor judgment from people who have legitimate access to your systems. What makes these threats so dangerous is that they derive from trusted users: your staff, volunteers, former employees, or even external partners with privileged access.
Whether intentional or accidental, insider actions can cause severe harm to your charity’s operations, data security, and reputation. Here are a few practical examples of potential insider threats in cybersecurity:
- An angry employee steals sensitive donor data before leaving the organisation, potentially violating GDPR and exposing your supporters to fraud.
- A staff member manipulates the system configurations, either out of frustration or as a form of revenge, which prevents essential services from running as normal.
- A former employee still has access to internal systems because offboarding procedures weren’t followed properly and uses that access to delete files or leak restricted information.
- An external IT contractor secretly installs a hidden backdoor, allowing them to regain access remotely after the project ends, without your knowledge.
- An employee under pressure or bribed by a third party knowingly clicks on a malicious link, which installs malware across your network.
These aren’t imaginary risks. They happen across all sectors and charities are no exception. In fact, the very trust-based culture of many nonprofits can make them more vulnerable, especially if internal security protocols are informal or archaic.
Understanding the Types of Insider Threats
Not all insider threats look the same. Some are intentional, others are entirely accidental and some come from people who don’t even realise they’re being manipulated. To protect your charity successfully, it’s crucial to understand the different types of insider threats and the risks they carry.
Here are the three main categories you need to know:
1. Malicious Insider Threats
These are individuals who deliberately set out to harm your organisation. Their motivations can vary, from personal grievances to financial gain to even ideological reasons, but their actions are intentional. They might steal sensitive data, leak donor and customer information, or sabotage your systems from within.
2. Negligent Insider Threats
This group includes well-intentioned staff or volunteers who make mistakes, like falling for a phishing email scam or a social engineering attack, using weak passwords, or losing an unencrypted laptop. These incidents aren’t malicious, but they still expose your charity to major risks, including data breaches and operational disruption.
3. Compromised Insider Threats
In this scenario, the individual’s account is hijacked by an external attacker. Cybercriminals use stolen login credentials to impersonate a legitimate user, allowing them to move through your systems unnoticed.
While all three types can be destructive, malicious and compromised insiders tend to cause the most severe and expensive breaches. But understanding the risks is the first step to put safeguards in place to protect your charity’s people, data, and mission.
Which Type of Insider Threat Carries the Highest Risk to Nonprofit Organisations?
Compromised Insider: Critical Risk
Compromised insiders are also a major concern. Since attackers operate under trusted credentials, their activities often bypass basic security checks. If an attacker gains entry to your network using legitimate credentials, they can move through systems unnoticed, exfiltrating data, installing malware, or disrupting your charity operations.
These threats often bypass traditional security tools and rely on the charity not having strong identity and access management in place.
Malicious Insiders: High Risk
Among the three types, malicious insiders pose the most dangerous threat to nonprofit organisations. Their actions are not accidental; they’re calculated and deliberate. Because they know your systems and security gaps, malicious insiders can do serious damage before anyone notices.
This dangerous combination, their deliberate intent, system knowledge, and access to sensitive information make them extremely dangerous and difficult to detect until the damage is already done.
In a charity setting, where trust is an underlying part of the culture, a malicious insider can operate undetected for longer. They might gain access to donor databases, grant information, financial records, or even trustee communications. If they choose to exploit that access, the fallout could be devastating, from reputational harm to loss of funding and compliance violations.
Negligent Insiders: Moderate Risk
The risks from negligent insiders are not to be taken too lightly. A volunteer reusing a weak password, or an employee forwarding a sensitive email to the wrong recipient, can open the door to equally damaging breaches. These threats are familiar and difficult to eliminate completely, especially without ongoing security awareness training.
Each type presents a real and growing threat. That’s why it’s vital to understand all three and build a layered defence that covers people, processes, and technology.
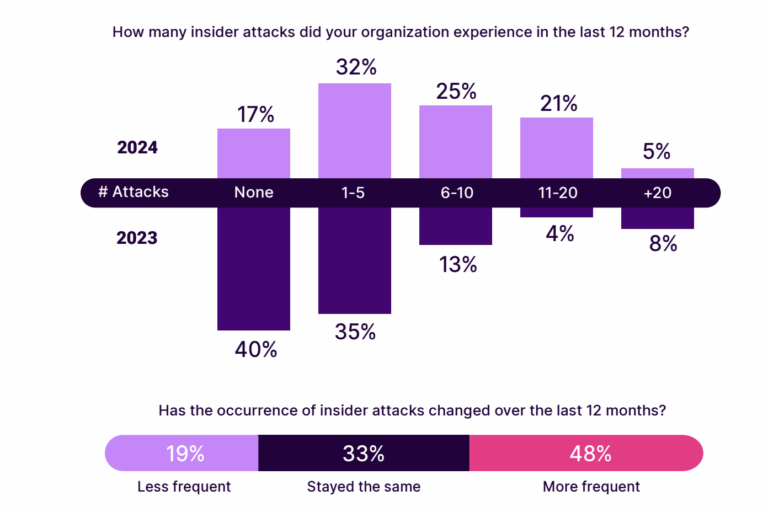
Why Charities Can’t Afford to Ignore Insider Threats
Charities are becoming increasingly digital by the day, embracing cloud solutions, remote collaboration tools, and online fundraising platforms to better serve their communities (here’s why digital transformation matters). But while digital transformation brings many benefits, it also comes with some risks, such as increased exposure to cyber attacks. This is why cybersecurity measures for nonprofits are non-negotiable.
A single insider incident can create a ripple effect, damaging trust, draining finances, and threatening your ability to deliver your mission. Here are the main reasons charities should watch out for insider threats:
- Financial Impact
- Direct Theft
- Operational Costs of a Breach
- Loss of Future Donations
- Reputational Damage and Loss of Trust
- Compromise of Sensitive Donor and Beneficiary Data
- Operational Disruption
- Slow Recovery
- Compliance and Governance Requirements
Financial Impact
Insider threats hit charities where it hurts most: limited resources. The financial toll of responding to a breach can be expensive, diverting funds away from the very people and causes you’re trying to support.
Beyond direct breach response, a serious security incident can disrupt your daily operations. This could include lost productivity from staff dealing with the fallout, inability to access critical systems, or even the temporary suspension of services. Every hour spent recovering is an hour not spent fulfilling your charitable goals, which results in financial losses.
Direct Theft
Malicious insiders may abuse their access not just to leak data, but to directly steal from your charity, to divert donations, commit accounting fraud, or reroute supplier payments. These actions don’t just impact your balance sheet, they undercut every project relying on those funds.
Operational Costs of a Breach
Investigating a data breach, notifying those affected (often a legal requirement under GDPR), providing credit monitoring, covering legal fees, it all adds up fast. And it drains time and attention from your primary mission.
Loss of Future Donations
Once word spreads about a security lapse, supporters may think twice before giving again. Charities rely heavily on goodwill, and even a hint of mismanagement can have long-term consequences for fundraising.
Reputational Damage and Loss of Trust
Trust is the lifeblood of every nonprofit. Whether it’s individuals making monthly donations or major grant providers assessing due diligence, people give because they believe in you.
An insider incident, especially one involving leaked donor or beneficiary data, can be a PR crisis. With today’s media landscape, stories can spread quickly, and reputations built over years can unravel overnight.
Compromise of Sensitive Donor and Beneficiary Data
Data is pivotal to charity operations. Contact information, donation histories, personal stories, case files, this isn’t just information; it’s people’s lives and trust in your hands.
A breach not only risks emotional harm to those affected; it can also trigger critical regulatory consequences. Under the GDPR, charities must follow strict data protection standards. Non-compliance can result in fines and mandatory reporting to the ICO.
Make sure your charity is covered by reviewing our advice on data protection best practices.
Operational Disruption
Insider threats can go beyond data loss; they can bring your day-to-day operations to a halt. A compromised user might disable access to your email systems, tamper with records, or knock out your fundraising platforms.
When your systems go down, so does your mission delivery. Volunteers are unable to coordinate, campaigns can’t launch, and services can’t reach the people who need them.
Slow Recovery
While some organisations bounce back quickly, 45% take over a week to recover from an insider attack, according to recent reports. For charities, that’s a week of lost donations, stalled programmes, and reputational risk piling up.
Compliance and Governance Requirements
From donor records to beneficiary details and grant applications, charities hold highly confidential information. Regulators and funders are raising the bar on cybersecurity, and insider threats sit directly within that scope.
Fiduciary Duty
Trustees have a legal and ethical responsibility to defend their charity’s assets, including digital ones. Ignoring insider threats puts your organisation at risk of failing that duty.
Grant Requirements
More Grantmakers now expect documented cybersecurity policies and evidence of secure systems before funding is approved. A serious incident could endanger your eligibility and long-term funding relationships.
Closing Thoughts
Insider threats may not always make headlines, but they’re among the most treacherous risks facing charities today. Whether it’s a malicious insider with deep system access, a well-meaning staff member making a mistake, or an external attacker using compromised credentials, these threats can seriously damage your charity’s mission.
For charities, where trust, transparency, and every pound matter, the impact can be remarkably devastating. And with digital systems now integral to everything from fundraising to service delivery, the stakes have never been higher.
By understanding the different types of insider threats and their warning signs, your organisation can take preemptive steps to reduce the risks. That includes strengthening internal security teams, improving access controls, educating staff, implementing policies for using personal devices at work, and planning regular cybersecurity audits.
Does your charity need help preventing cyber threats or strengthening its cybersecurity posture?






